Can NFTs Be Malicious? | Revealing The Truth
NFTs are digital tokens that represent unique and scarce assets on the blockchain. They have become a popular way to create, buy, and sell digital art, collectibles, music, and more. ...
blog + security solutions + SOC Z. Oualid today
In the ever-evolving landscape of cybersecurity, the battle against malicious software is a relentless pursuit. As digital threats become more sophisticated, so must the arsenal of tools employed by cybersecurity experts. Today, we embark on a journey into the heart of this cyber battlefield, where hidden within lines of code and encrypted algorithms, a war wages between defenders and attackers.
Whether you’re an aspiring cybersecurity professional, a seasoned analyst, or simply intrigued by the complex dance between code and security, this post is your gateway to understanding the tools that keep our digital landscapes safe. So, buckle up as we navigate through the labyrinth of malware analysis tools, unraveling the mysteries and unveiling the secrets that empower defenders in the ongoing war against cyber threats. So what are the tools used in malware analysis and why?
Wireshark, a ubiquitous name in the realm of cybersecurity, stands as a linchpin in the arsenal of malware analysts, offering a powerful lens into the clandestine communications between systems. Deployed during the critical phase of network traffic analysis, Wireshark plays an instrumental role in deciphering the intricate dance of malicious software. As malware evolves to operate covertly and exploit network vulnerabilities, Wireshark emerges as a beacon of visibility, allowing analysts to intercept, record, and analyze real-time network traffic.
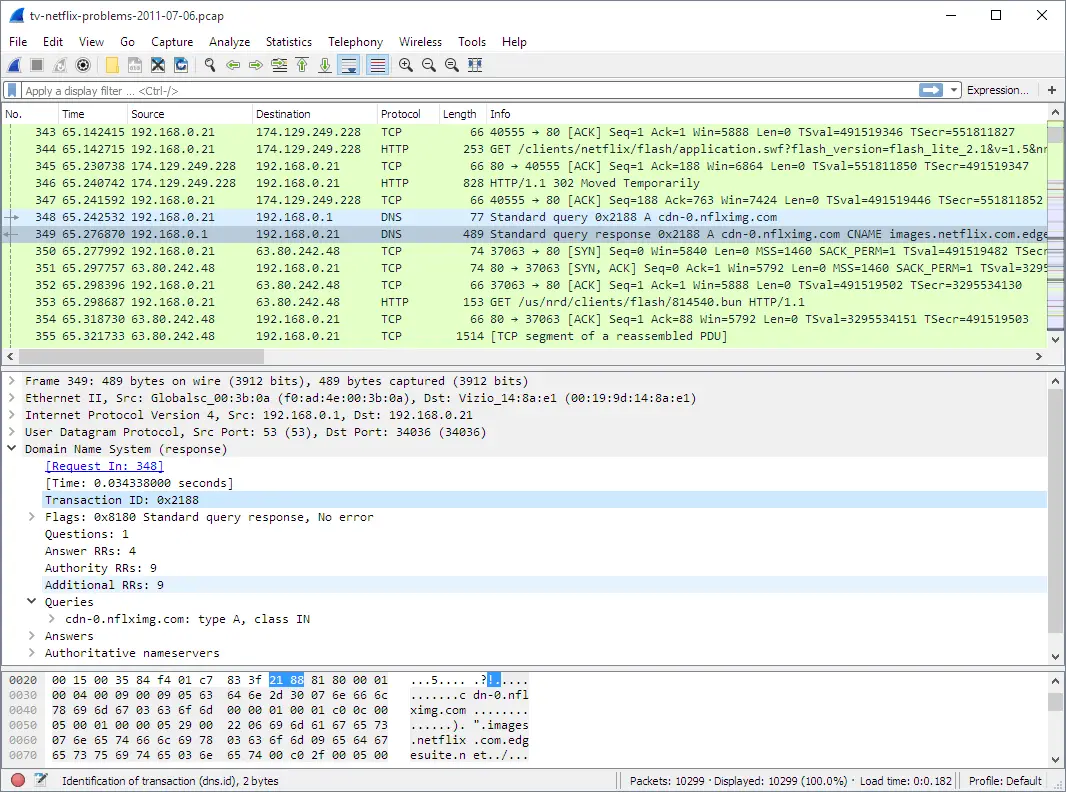
In the intricate ballet of cyber threats, Wireshark excels at capturing the subtle nuances that define malicious communication. It provides analysts with the ability to identify irregular patterns, unexpected destinations, and non-standard protocols, acting as a sentinel against the stealthy maneuvers of malware. As the initial line of defense, Wireshark aids in the swift detection of anomalous network activities, revealing the footprints of potential threats before they can fully manifest.
Wireshark’s importance extends beyond mere detection; it is a key player in understanding the behavior of malware within a network. By dissecting network packets, analysts can identify command and control connections, uncover data exfiltration attempts, and discern the tactics employed by malicious software to propagate. Wireshark’s real-time visibility into network activities empowers analysts to respond promptly to emerging threats, minimizing the potential impact of an infection and facilitating a more effective incident response.
Furthermore, Wireshark plays a vital role in evidence collection for forensic analysis. The captured network traffic serves as a digital breadcrumb trail, allowing analysts to reconstruct the sequence of events and actions taken by the malware. This capability is instrumental in piecing together the puzzle of an attack, supporting investigations, and providing a detailed account of the malware’s activities within the network.
In the ever-evolving landscape of cybersecurity, Wireshark remains an indispensable tool, providing analysts with a panoramic view of the cyber battleground. Its ability to unveil the covert conversations between systems offers a critical perspective in the ongoing battle against malware. Wireshark stands not just as a tool but as a sentinel, offering clarity in the face of digital obscurity and empowering cybersecurity professionals to safeguard digital ecosystems from the relentless advance of malicious software.
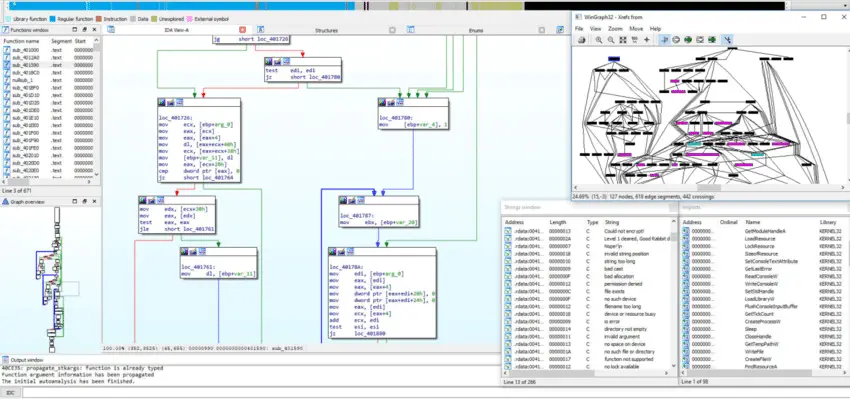
In the intricate landscape of cybersecurity, where the battle against malware demands a profound understanding of malicious code, IDA Pro stands as an indispensable ally for malware analysts. This sophisticated disassembler and debugger emerge as a beacon of insight during the static analysis phase, where the intricacies of a malware sample are dissected without execution. IDA Pro’s importance lies in its unparalleled ability to convert machine code into a human-readable assembly language, providing analysts with a comprehensive view of the binary logic.

IDA Pro comes to the forefront when unraveling the complex tapestry of malicious software. Its prowess in code disassembly lays bare the inner workings of malware, breaking down machine instructions into a decipherable assembly language. This process allows analysts to navigate through the labyrinth of code, unveiling the logic, functions, and potential malicious activities embedded within. The tool’s capability to identify and categorize functions within a malware sample enhances the granularity of analysis, providing a roadmap to understand the intricacies of the malicious code.
Beyond disassembly, IDA Pro plays a pivotal role in control flow analysis, aiding analysts in visualizing the intricate dance of program execution. Understanding the flow of control within a malware program is paramount, and IDA Pro’s graphical representation of control flow graphs allows analysts to pinpoint loops, conditionals, and critical points within the code. This visual mapping is instrumental in comprehending the malware’s logic and identifying potential vulnerabilities or areas of interest.
The importance of IDA Pro in malware analysis extends to its role in signature generation. Analysts often create signatures based on unique patterns or features identified in malware samples, contributing to the development of effective detection mechanisms. Moreover, IDA Pro empowers analysts with reverse engineering capabilities, allowing for the modification or patching of the binary to neutralize its impact and inform the creation of countermeasures.
In conclusion, IDA Pro stands as a cornerstone in the toolkit of malware analysts, providing a lens through which the intricate language of malicious code is decoded. Its role in disassembly, function identification, control flow analysis, signature generation, and reverse engineering makes it an essential companion in the relentless pursuit to understand, counter, and neutralize the evolving threats posed by malware in the digital landscape.
In the intricate world of cybersecurity, where identifying and categorizing emerging threats is akin to solving a complex puzzle, the YARA tool emerges as a detective’s magnifying glass for malware analysts. YARA, an acronym for Yet Another Recursive Acronym, is a powerful and flexible pattern-matching tool designed to identify and classify malware based on predefined rules or signatures. Its significance becomes apparent during the early stages of malware analysis, specifically in the static analysis phase.

YARA is the vigilant sentinel at the forefront of signature-based detection, offering cybersecurity analysts a meticulous lens to peer into the heart of potential threats. During static analysis, where the examination of a malware sample without execution is paramount, YARA’s ability to define and apply specific patterns or characteristics associated with known malware families becomes invaluable. By creating custom rules, analysts can swiftly and accurately identify the unique fingerprints left by malicious code, enabling the proactive detection of threats that might otherwise go unnoticed.
The importance of YARA transcends mere identification; it actively contributes to the development of threat intelligence. As analysts create and refine YARA rules based on patterns observed in malware samples, this intelligence becomes a sharable resource within the cybersecurity community. The collaborative nature of YARA’s rule-sharing enhances collective defenses, fortifying the broader landscape against the ever-evolving tactics of malicious actors.
YARA’s versatility extends its impact beyond just static analysis. It empowers analysts to adapt and extend rule sets as new threats emerge, ensuring that detection mechanisms remain agile in the face of evolving malware tactics. The tool’s flexibility, coupled with its capacity to identify both known and potentially novel threats, solidifies its place as a foundational element in the malware analyst’s toolkit.
In conclusion, YARA stands as a force multiplier in the intricate dance between cybersecurity defenders and malicious actors. Its role in static analysis, signature-based detection, and the collaborative generation of threat intelligence elevates it to a crucial position in the ongoing battle against cyber threats. YARA not only aids in swift identification but also fosters a community-driven defense, where collective knowledge becomes the key to staying ahead in the perpetual cat-and-mouse game of cybersecurity.
In the relentless pursuit of understanding and combatting cyber threats, the Volatility tool emerges as a beacon of insight, specifically in the realm of memory forensics for malware analysis. Developed in Python, Volatility stands as an indispensable asset for cybersecurity professionals seeking to uncover the hidden traces of malicious activities within a system’s volatile memory. Its significance becomes evident during the dynamic analysis phase, where analysts delve deep into the runtime behavior of malware to discern its tactics, techniques, and procedures.
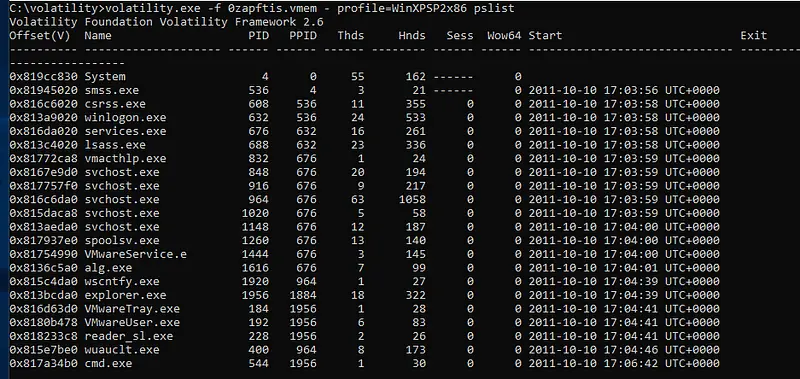
Volatility’s prowess lies in its ability to extract valuable information from the volatile memory of a computer system, providing a dynamic and real-time perspective on the activities of malicious software. During the execution of a malware sample, Volatility serves as a virtual microscope, capturing crucial artifacts such as running processes, network connections, and injected code within the system’s RAM. This detailed view into the memory landscape allows analysts to observe the true impact of the malware, unraveling its behaviors and shedding light on the intricacies of its operation.
The tool excels in critical aspects of memory forensics, including process and network analysis. Analysts can dissect running processes, identify code injection techniques, and trace the relationships between different components of the malware. Volatility’s capability to analyze network artifacts within memory unveils communication channels, command and control servers, and data exchanged between the malware and external entities, providing a comprehensive picture of the malware’s network interactions.
Furthermore, Volatility plays a pivotal role in constructing a forensic timeline of events. By examining memory dumps, cybersecurity professionals can trace the evolution of the malware, understand the sequence of actions taken during an infection, and ultimately reconstruct a detailed narrative of the threat’s lifecycle. This capability enhances incident response efforts, enabling analysts to develop precise and effective strategies for containment, eradication, and mitigation.
In essence, Volatility stands as a digital archaeologist’s toolkit, unearthing the hidden artifacts within a system’s volatile memory and empowering analysts to dissect, understand, and neutralize the threats posed by malicious software. As the digital landscape evolves and adversaries become more sophisticated, Volatility remains an essential instrument in the hands of defenders, allowing them to navigate the intricate terrain of memory forensics and fortify their defenses against the ever-changing threat landscape.
In the intricate landscape of malware analysis, understanding the inner workings of malicious code is paramount, and tools like OllyDbg and x64dbg stand out as indispensable assets in this quest. These dynamic analysis tools serve as debuggers, allowing cybersecurity analysts to scrutinize the execution flow, dissect the assembly code, and gain insights into the behavior of malware samples.
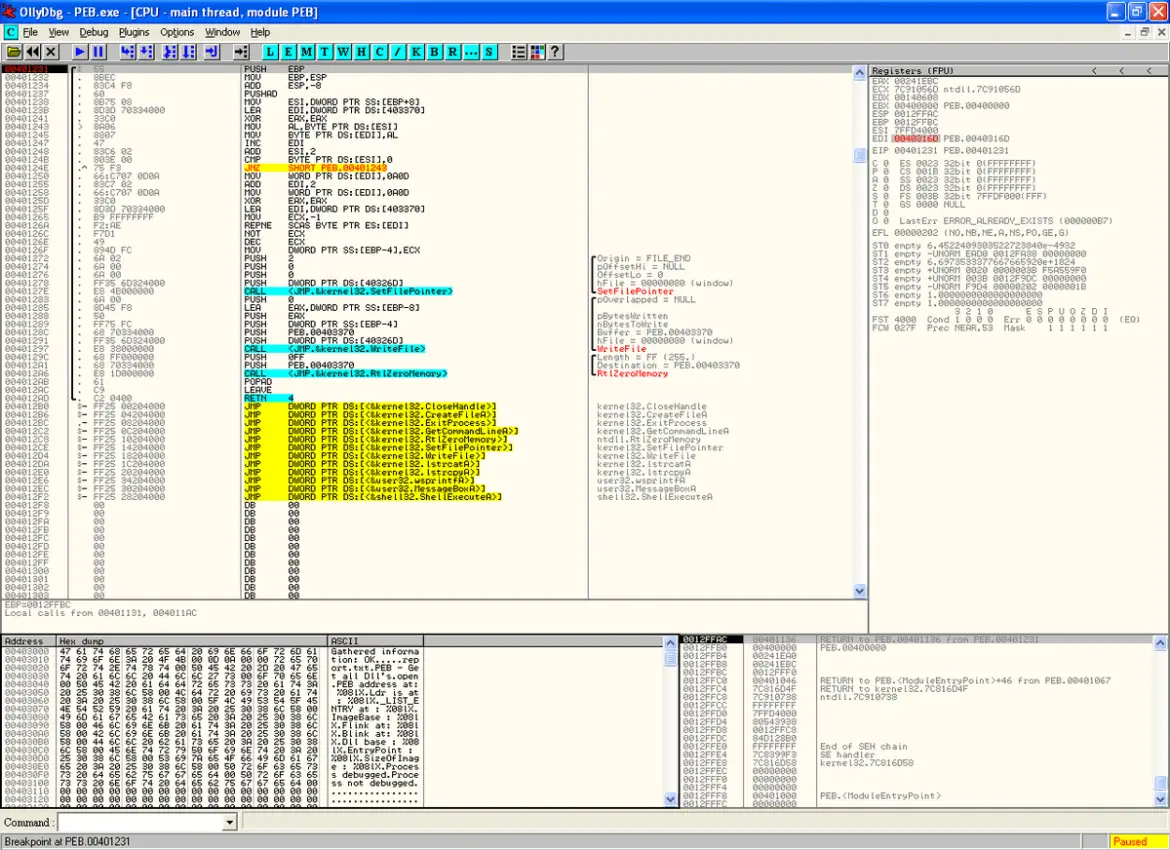
OllyDbg and its successor, x64dbg, are revered for their prowess in dynamic analysis, a phase where analysts delve into the runtime behavior of malware. This crucial step involves executing the malware within a controlled environment, enabling researchers to observe its actions, interactions with the system, and the manipulation of data in real-time.
One of the primary functions of OllyDbg/x64dbg is to unravel the obfuscation and encryption layers employed by malware creators to hide their intent. Analysts can set breakpoints, step through the code, and inspect the values of registers and memory, allowing them to decipher the logic of the malware and identify key functions and routines. This level of visibility into the runtime behavior is instrumental in comprehending the intricacies of the malicious code, aiding analysts in uncovering the malware’s capabilities, potential payloads, and evasion techniques.
Furthermore, OllyDbg/x64dbg provides a dynamic environment for code modification, enabling analysts to patch or manipulate the malware’s behavior during runtime. This capability is invaluable for researchers seeking to understand the impact of different inputs or to neutralize certain aspects of the malware for further analysis.
In the ever-evolving landscape of cyber threats, the importance of dynamic analysis tools like OllyDbg and x64dbg cannot be overstated. Their role in uncovering the behavioral patterns, logic, and evasion tactics employed by malware samples contributes significantly to the broader efforts of cybersecurity professionals in detecting, understanding, and mitigating evolving threats. As malicious actors continue to advance their techniques, the significance of robust dynamic analysis tools like OllyDbg/x64dbg becomes increasingly crucial in fortifying digital defenses.
In the intricate landscape of cybersecurity, the ability to swiftly identify and categorize potential threats is paramount, and PEiD emerges as a crucial tool in the arsenal of malware analysts. PEiD, which stands for PE Identifier, is specifically designed to analyze and identify the packers or compilers used in the creation of executable files. This tool proves indispensable during the initial stages of malware analysis when understanding the origin and characteristics of a file is critical.
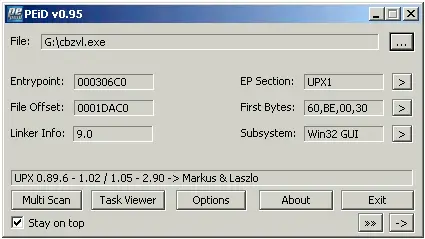
PEiD comes into play during the static analysis phase, where analysts examine the binary code without executing the malware. Malicious actors often employ packers or compressors to obfuscate their code, making it challenging for traditional signature-based detection methods to identify known threats. PEiD, however, shines in this scenario by providing insights into the packing techniques utilized, allowing analysts to unmask the hidden code within the executable.
The importance of PEiD lies in its ability to reveal the “fingerprint” left by packers, offering valuable clues about the malware’s origin and sophistication. By identifying the specific packer or compiler used, analysts gain a deeper understanding of the threat landscape, including potential affiliations with known malware families or threat actor groups. This information is pivotal in tailoring effective mitigation and response strategies.
Moreover, PEiD contributes to the broader context of threat intelligence. As analysts create signatures and profiles based on the packers identified, this information can be shared across the cybersecurity community, enhancing collective defense efforts. The collaborative nature of threat intelligence is strengthened by PEiD’s role in illuminating the diverse range of packers employed by malicious software.
In conclusion, PEiD stands as a linchpin in the realm of malware analysis, offering a lens through which analysts can decipher the intricate layers of obfuscation deployed by cyber adversaries. Its ability to unmask the concealed elements within executable files not only aids in the identification of potential threats but also plays a pivotal role in the collaborative effort to fortify digital defenses and stay one step ahead of evolving cyber threats.
In the ever-expanding battlefield of cybersecurity, where the war against malware is fought on multiple fronts, network security plays a pivotal role. Enter Snort, an open-source intrusion detection and prevention system that stands as a stalwart guardian on the network frontier. Snort is not merely a tool; it is a sentinel that tirelessly monitors network traffic, acting as a first line of defense against potential threats. It comes to the forefront of malware analysis when real-time detection and prevention of malicious activities on the network are paramount.
Snort is deployed during the network traffic analysis phase, where its importance becomes evident in identifying and responding to potential malware infections. This tool excels in the nuanced task of intrusion detection, where it scrutinizes packets traversing the network for patterns indicative of known attack signatures or malicious behaviors. By leveraging a vast rule set that encompasses diverse threat intelligence, Snort can swiftly detect and alert security teams to suspicious activities, including communication with known command and control servers, unusual network traffic patterns, or attempts to exploit vulnerabilities.
The significance of Snort lies not only in its ability to detect malicious activities but also in its role as an effective preventive measure. By alerting security teams in real-time, Snort empowers them to respond promptly to potential threats, minimizing the impact of malware on the network. Its capabilities extend beyond mere detection, as Snort can be configured to block or mitigate malicious traffic, acting as a proactive shield against cyber threats.
Furthermore, Snort contributes to threat intelligence by generating detailed logs and alerts that can be analyzed to understand the evolving tactics and techniques employed by malicious actors. This wealth of information enhances the overall situational awareness of cybersecurity professionals, enabling them to adapt defenses and stay ahead of emerging threats.
In essence, Snort emerges as a crucial component in the arsenal of cybersecurity defenders, offering a vigilant eye on the network’s traffic and fortifying the digital perimeter against the relentless onslaught of malware. Its real-time detection and prevention capabilities, coupled with its contribution to threat intelligence, position Snort as a frontline defender in the ongoing battle to secure digital ecosystems against evolving cyber threats.
In the intricate realm of malware analysis, where every clue counts in deciphering the tactics and impact of malicious software, the importance of tools like RegShot cannot be overstated. RegShot, a registry compare utility, serves as a forensic lens, allowing cybersecurity analysts to scrutinize and track changes made to the Windows registry during the execution of a file. This tool comes into play during the vital stage of registry analysis, offering a meticulous snapshot of registry modifications before and after the execution of a suspected malware sample.
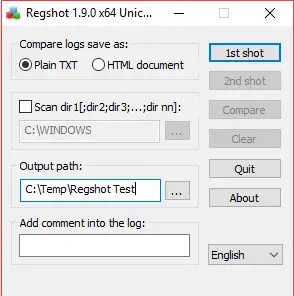
RegShot proves its worth during the static analysis phase, where understanding the alterations made to the Windows registry by a malware sample is critical. Malicious software often manipulates the registry to achieve persistence, disguise its presence, or make system-level modifications. RegShot captures a comprehensive before-and-after snapshot of the registry, enabling analysts to discern the specific changes induced by the malware.
The significance of RegShot lies in its ability to streamline the identification of registry-based indicators of compromise (IOCs). By comparing the registry states, analysts can pinpoint alterations such as new startup entries, changes to critical system configurations, or the creation of malicious keys. These insights not only aid in understanding the impact of the malware but also provide actionable intelligence for developing mitigation and remediation strategies.
Moreover, RegShot plays a crucial role in the larger context of digital forensics. Its detailed reports serve as a historical record of registry changes, contributing to the reconstruction of events during a malware infection. This capability enhances the investigative process, allowing analysts to trace the evolution of the threat and providing a foundation for comprehensive incident response.
In conclusion, RegShot emerges as a key instrument in the toolkit of cybersecurity professionals, offering a focused lens on the subtle but impactful changes a malware sample introduces to the Windows registry. Its role in capturing and comparing registry states not only aids in the precise identification of malicious activities but also serves as a valuable resource in the broader efforts of digital forensics and incident response. In the perpetual quest to understand and combat malware, RegShot stands as an invaluable ally, unveiling the intricate footprints left by malicious actors within the heart of the Windows operating system.
In the dynamic landscape of cybersecurity, where malware constantly evolves to elude detection, tools like Sysinternals Suite, featuring gems like Process Explorer and Autoruns, emerge as beacons for malware analysts. This suite stands as an indispensable resource, offering unparalleled visibility into the intricate processes and autostart mechanisms of a system. Deployed during the dynamic analysis phase, Sysinternals Suite plays a pivotal role in unraveling the activities of malicious software.
Process Explorer, a flagship tool within Sysinternals Suite, acts as a forensic microscope, providing an in-depth examination of running processes. Analysts can peer into the hierarchical structure of processes, explore their associated DLLs, and scrutinize network connections and loaded modules. This level of granularity is essential for identifying malicious processes, understanding their relationships, and uncovering potential code injection or manipulation within the system.
Complementing Process Explorer, Autoruns sheds light on the autostart entries in a system, including registry keys, startup folders, and scheduled tasks. Malware often employs autostart mechanisms to persist on an infected system, and Autoruns serves as a detective, exposing these subtle but critical elements. Analysts can navigate through an extensive list of autostart locations, enabling them to identify and disable malicious entries, ultimately thwarting the persistence mechanisms employed by malware.
The importance of Sysinternals Suite in malware analysis lies in its ability to offer a comprehensive and real-time view of system activities. Analysts can uncover the clandestine operations of malware, whether it’s concealing its presence within legitimate processes or establishing persistence through cunning autostart methods. The suite’s detailed insights empower analysts to make informed decisions, swiftly identify and neutralize threats, and fortify the defenses of digital ecosystems.
Moreover, the Sysinternals Suite is an invaluable educational resource for malware analysts and security practitioners, fostering a deep understanding of Windows internals. As the cyber threat landscape continues to evolve, Sysinternals Suite remains an essential companion, illuminating the shadows where malware lurks and providing a powerful lens for those committed to dissecting and understanding the tactics of digital adversaries. In the ongoing battle against malware, Sysinternals Suite stands as a beacon of visibility, enabling defenders to navigate the complexities of the digital landscape with precision and insight.
In the intricate realm of cybersecurity, where the battle between defenders and malicious actors rages on, the FireEye Malware Analysis tool emerges as a formidable ally in deciphering the intricacies of digital threats. Deployed during the critical phase of dynamic analysis, this tool plays a pivotal role in unveiling the concealed tactics, behaviors, and capabilities of malware. Its importance lies in its advanced capabilities, offering cybersecurity professionals a sophisticated platform to dissect, understand, and ultimately neutralize the threats posed by malicious software.

The FireEye Malware Analysis tool comes to the forefront when analysts seek to unravel the elusive nature of malware, particularly during the dynamic analysis phase. By executing a suspected malware sample within a controlled environment, the tool provides real-time insights into the behavior of the malicious code. Its robust features allow analysts to monitor system interactions, identify network communications, and scrutinize the various techniques employed by malware to evade detection and execute its objectives.
Crucially, the tool aids in the identification of novel and previously unseen threats. Leveraging its extensive threat intelligence databases and advanced detection mechanisms, FireEye Malware Analysis contributes to the identification of emerging malware variants, zero-day threats, and advanced persistent threats (APTs). This proactive approach to threat detection is paramount in staying ahead of cyber adversaries who constantly refine their tactics to bypass traditional security measures.
Moreover, FireEye Malware Analysis supports the development of Indicators of Compromise (IOCs) that serve as digital fingerprints for identifying and tracking malicious activities. The rich contextual information provided by the tool assists in crafting comprehensive incident reports, enhancing incident response efforts, and ultimately fortifying the resilience of digital ecosystems against evolving cyber threats.
In conclusion, the FireEye Malware Analysis tool stands as a beacon in the fight against cyber threats, offering cybersecurity professionals an advanced and comprehensive platform to dissect and understand the nuances of malware. Its role in dynamic analysis, threat intelligence, and the identification of novel threats solidifies its importance in the arsenal of defenders, enabling them to navigate the shadows of the digital landscape and respond effectively to the relentless evolution of malicious software.
Each tool in this arsenal serves a unique purpose, collectively forming a comprehensive defense against the dynamic and ever-expanding landscape of cyber threats. As the digital battleground continues to evolve, these tools stand as indispensable resources, empowering cybersecurity professionals to navigate the complexities of malware analysis with precision, insight, and resilience. In this ongoing saga, the synergy between defenders and their tools remains paramount, ensuring that the digital realm remains a secure and resilient space for users worldwide.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

Blockchain Security Z. Oualid
NFTs are digital tokens that represent unique and scarce assets on the blockchain. They have become a popular way to create, buy, and sell digital art, collectibles, music, and more. ...



today
blog + secure coding + security solutions + Smart contract Z. Oualid
Undoubtedly, ChatGPT stands out as one of the most remarkable inventions of 2021. Its wide-ranging capabilities and applications have opened up endless possibilities for human interaction and problem-solving. Furthermore, certain [...]
Copyright © 2020 Getsecureworld.
Post comments (0)