
How To Remove A Ransomware ? | Step By Step
Ransomware is a type of malicious software designed to encrypt a user’s files or entire system, rendering them inaccessible until a ransom is paid to the attacker which can cause ...
blog + secure coding + Smart contract + Solidity Z. Oualid today

Smart contracts, integral to any decentralized application (Dapp) on the Blockchain, autonomously enforce predefined conditions when specific criteria are met, eliminating the necessity for intermediaries in contract execution. Despite their decentralized advantages, smart contracts have increasingly attracted attention from malicious actors seeking financial gains. Consequently, the question arises: Can a smart contract be DDOSed?
Smart contract can be DDoSed due to either a successful exploitation of DoS vulnerability in its source code or an unpredictable array length growing. In addition, the DDoS attack could target the Blockchain where the smart contract is deployed which will cause a DoS on the smart contract.
In this blog post, we will provide a comprehensive exploration of how such attacks can occur, even within the framework of a distributed system. The discussion will include illustrative code examples highlighting common vulnerabilities and bugs associated with this type of attack. If you’re eager to deepen your understanding of this topic, simply continue reading for valuable insights.
A DDoS attack in Blockchain occurs when the network is unable to process new transactions from clients for a certain duration. Despite a common misconception that Blockchain is immune to DDoS attacks due to its decentralized architecture, this belief is rooted in a myth. While the distributed nature of Blockchain safeguards against traditional DDoS attacks targeting network traffic, attackers exploit vulnerabilities in various components of the Blockchain network, aiming to disrupt its operations and compromise functionality. Contrary to saturating bandwidth, attackers focus on undermining specific layers of the OSI model, posing a distinct challenge in the context of Blockchain DDoS attacks.
As we have explained in the previous blog post, DoS attack could also happen at the application layer of the Blockchain. A dos attack could also happen due to a smart contract exhausting all available gas before completing its execution.
Each smart contract on the Blockchain has a limited gas supply, and users must specify a fixed gas limit for proper execution. If the user’s specified gas is depleted before the contract finishes, the transaction is reversed, and the gas is not refunded.
This attack, often triggered by a smart contract bug, can persist irrespective of user-specified gas limits, leading to a denial-of-service (DoS) scenario. For instance, a smart contract managing user accounts may face a DoS attack if a user creates numerous accounts, causing the contract to run out of gas before completing essential operations like funding.
Denial-of-Service (DoS) attacks on smart contracts can also arise from conditions that are perpetually true or false, preventing the execution of essential functions within the contract. This vulnerability often stems from flaws in the contract’s logic, such as the implementation of modifiers in Solidity. Consider a scenario where a modifier, a crucial part of a contract’s function, is inadvertently set to always evaluate as false.
Modifiers in Solidity act as conditions that must be satisfied for a function to proceed. If, due to an error or oversight, a modifier consistently evaluates to false, it becomes impossible for the associated function to execute its necessary operations.
For instance, a modifier intended to check certain conditions before allowing fund transfers might be unintentionally coded to always return false. In this case, any attempt to execute the corresponding function will be denied, creating a situation akin to a DoS attack.
Attackers may intentionally exploit such vulnerabilities or, in some instances, these conditions may be inadvertently introduced during the contract development process. Ensuring the logical soundness of modifiers and conditions is paramount to preventing these types of DoS attacks and maintaining the integrity and functionality of smart contracts on the blockchain.
In this section of the blog post we are going to give you some realistic examples of vulnerabilities or bugs in smart contract that leads to DoS attacks.
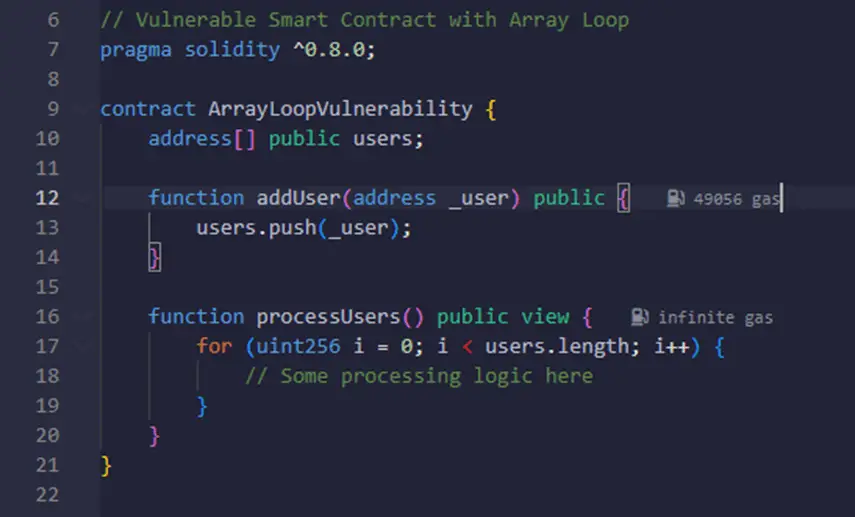
In this example, the processUsers function processes an array of users stored in the smart contract. However, if an attacker repeatedly calls the addUser function with new addresses, the array will continuously grow, leading to an excessively long loop in the processUsers function. As a result, the smart contract’s gas will be depleted before completing the loop, creating a Denial-of-Service (DoS) vulnerability.
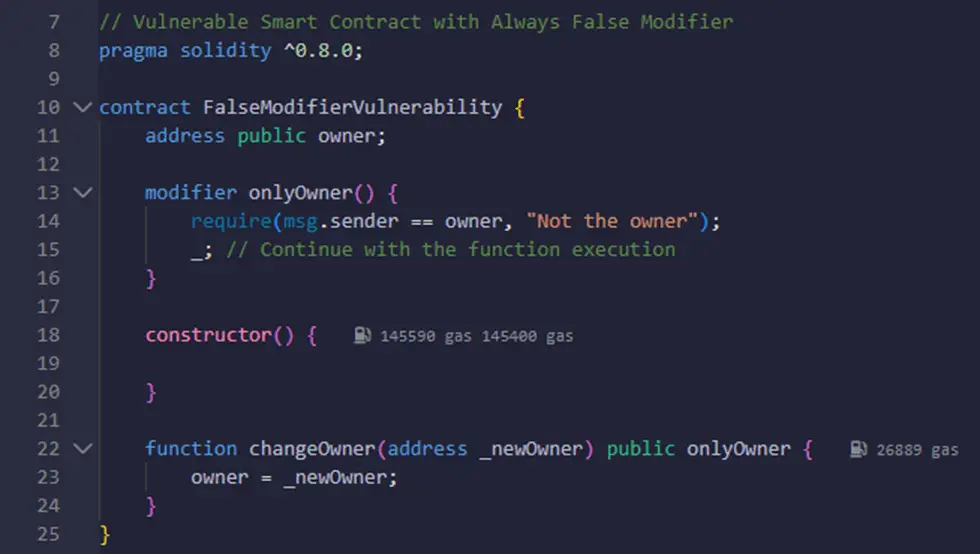
In this example, the onlyOwner modifier is intended to restrict access to certain functions to only the contract owner. However, due to a logical error, the modifier always returns false. As a result, any attempt to execute functions with the onlyOwner modifier, such as changeOwner, will fail regardless of the actual sender’s address. This creates a DoS vulnerability, as the intended functionality of the contract is hindered by the perpetually false modifier condition.
DoS attacks are very destructive especially in the Blockchain context. A DoS vulnerability in a smart contract will remain their forever and there is no way to fix it due to its immutability. Therefore, this kind of vulnerabilities should be avoided before going to the production. Here is some of the things that you can do to fix this kind of issues:
To mitigate the risk of Denial-of-Service (DoS) attacks caused by uncontrolled array length based loops, it is crucial to implement safeguards in smart contracts. Developers should consider incorporating limits or constraints on array lengths, ensuring that loops are bounded and cannot be exploited to exhaust gas.
Implementing checks on the size of arrays and incorporating mechanisms to prevent unchecked growth can significantly enhance the resilience of smart contracts against malicious attempts to flood arrays with infinite inputs.
By carefully managing array lengths and adopting defensive programming practices, developers can create more robust and secure smart contracts that resist potential vulnerabilities associated with uncontrolled loop iterations.
Performing an automated scan using a reliable smart contract vulnerability scanner is a proactive approach to fortify smart contracts against potential issues that may lead to Denial-of-Service (DoS) attacks.
These scanners employ advanced techniques to analyze smart contract code, identifying vulnerabilities such as uncontrolled loops, gas-exhaustion vulnerabilities, and other weaknesses that could be exploited for DoS attacks.
By leveraging automated scans, developers can systematically review and enhance the security posture of their smart contracts, ensuring robust protection against malicious attempts to disrupt contract functionality. Regular scans with sophisticated tools provide an efficient means to preemptively detect and address vulnerabilities, fostering a more resilient and secure blockchain ecosystem.
Complementing automated scans with a manual audit is a crucial step in fortifying smart contracts against potential issues that could lead to Denial-of-Service (DoS) attacks. While automated scanners excel at identifying common vulnerabilities, manual audits conducted by experienced blockchain security experts provide a nuanced and context-specific analysis. Human expertise can uncover subtle vulnerabilities that automated tools might overlook and assess the overall logic and architecture of a smart contract.
By combining the precision of automated scans with the critical thinking and domain knowledge of a manual audit, developers can ensure a comprehensive examination of their smart contracts, addressing potential weaknesses and creating a more robust defense against DoS attack vectors.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

blog Z. Oualid
Ransomware is a type of malicious software designed to encrypt a user’s files or entire system, rendering them inaccessible until a ransom is paid to the attacker which can cause ...



today
blog + secure coding + security solutions + Smart contract Z. Oualid
Undoubtedly, ChatGPT stands out as one of the most remarkable inventions of 2021. Its wide-ranging capabilities and applications have opened up endless possibilities for human interaction and problem-solving. Furthermore, certain [...]
Copyright © 2020 Getsecureworld.
Post comments (0)