Is your mobile app safe from attackers ?
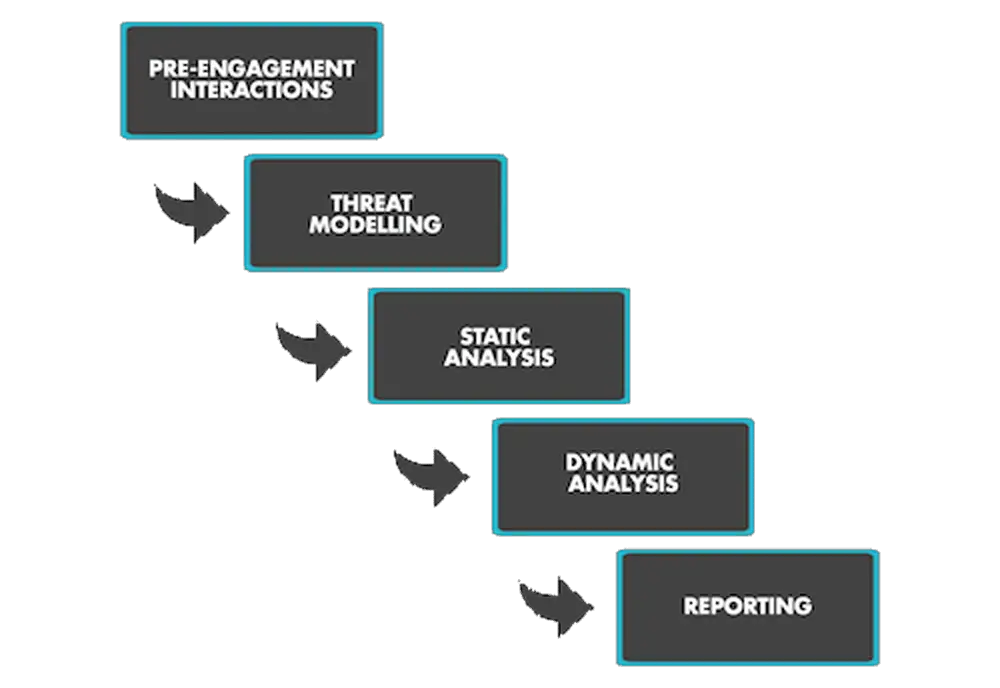
Both business and public organizations today are using mobile apps in new and compelling ways, from banking applications to healthcare platforms. Managing security risk is a growing challenge on these platforms, with new vulnerabilities found every day. Is your mobile app safe from attackers ?
Getsecureworld team offers top-tier mobile app penetration testing services, providing a holistic risk assessment to your mobile application. With industry-leading researchers and security engineers in both iPhone and Android, we provide deep dive testing into local, on-device security issues, back-end web services, and the API’s which connect them.