
Does the SEC575 certification worth it?
Performing a penetration test against a mobile application before releasing it to the public is becoming more and more necessary to protect the user’s personal life. Compared to classic web ...
Blockchain Security + blog Z. Oualid today
Blockchain technology was indeed built with security in mind. This means that it is supposed to be very secure compared to other technologies. However, Blockchain technology suffers from some weaknesses that can be exploited to damage the system. So what are Blockchain attacks?
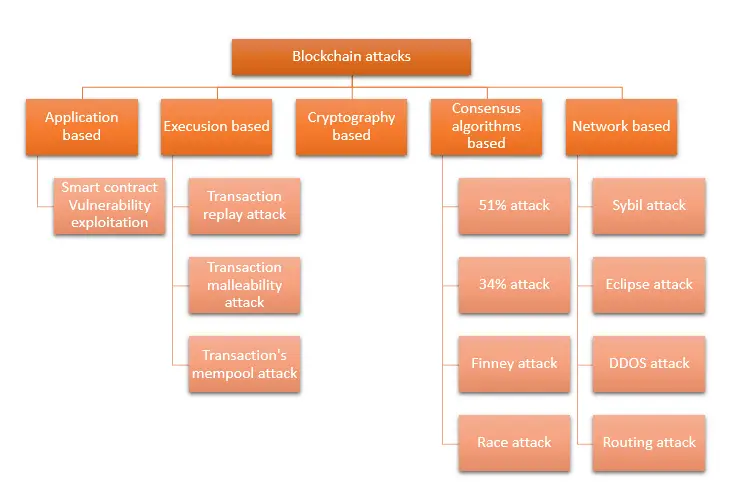
Blockchain technology could be attacked at each one of its layers. Each layer has specific technical limitations that could be used to perform attacks that may lead to manipulating or simply damaging the system. Here is a list of the Blockchain attacks ranked by layers:
As I said in the previous paragraph, the Blockchain system has different types of attacks that depend on the layers being targeted. Therefore, in this blog post, I am going to explain in detail what are the attacks that can be performed against every layer of the Blockchain and the way they work. So if you are interested in knowing more about this subject then just keep reading.
Before we start digging deeper into this subject, I would like to give you a macro view of the different attacks and what category they belong to.

The Cryptography based attacks will not be discussed in this blog post as they were already well discussed in many other blogs on the web. In addition, cryptography attacks are known to the community way before Blockchain technology get invented.
Smart contracts are the last layer in the Blockchain system. They are programs that implement the business logic and that run forever. Therefore, as the development technology of those programs is still immature compared to classic application technologies, they are usually deployed with critical vulnerabilities that can be exploited.
Similar to classic applications, some vulnerabilities are not very harmful. However, others are very critical and could lead to some serious business losses. What makes this kind of attack even more dangerous is their ease of exploitation. Attacks usually do not need a deep understanding of how to write a smart contract to exploit them. A simple transaction with the right parameters could easily lead to successfully exploiting the vulnerability.
The DAO attack is one of the most popular and successful smart contract vulnerability exploitation. This attack resulted in $1.25 million loss and was the may reason behind an Ethereum hard fork.
If you want to learn more about those attacks I highly encourage you to take a look at the following smart contract vulnerabilities and attacks discussed in previously written blog posts:
You should keep in mind that smart contract programs are immune, which means they cannot be changed once deployed. Therefore, a vulnerability discovered in a smart contract will remain in the smart contract for the whole Blockchain lifetime.
Most known Blockchain attacks nowadays are coming from vulnerable smart contracts as they are the first line that communicates directly with users.
The idea behind the transaction replay attack is to reuse the same transaction twice or more. Imagine that you have a wallet with 10 Ethers in the Ethereum main chain. Then for some reason, the Ethereum Blockchain has forked into Ethereum1 and Ethereum2.
Let’s say that you send 5 ethers from your wallet to another user and you broadcast this transaction in the Ethereum1 chain. Then if the Ethereum2 Blockchain does not put in place transaction replay attacks protection, an attacker will copy your transaction broadcasted in the Ethereum1 and broadcast it again in the Ethereum2 Blockchain.
The format of the user’s digital signatures used as part of the hash to sign the transaction is important. That format wasn’t always thoroughly examined. This meant that a poorly structured one may be introduced and yet be approved. It is feasible to generate several hashes for the same transaction by changing the signature in this manner. The idea here is to push users to perform multiple transactions by pretending to not receive them.
For more details about this attack, I highly encourage you to take a look at the following blog post as they well explained the attack.
The transaction mempool is a limited memory of transactions that are already verified but are waiting to get included in a block. The size of that memory is limited and transaction that does not have a place in the mempool will get dropped.
Therefore, an attacker could create a DOS in the Blockchain if he sends multiple fake transactions to the network to the point that it saturates that memory. This attack is a proof that the Blockchain system is also vulnerable to DOS attacks. In the following sections, I will show you that DOS attacks could be performed against a Blockchain in different manners depending on the Blockchain layer the attacker target.
I have already explained the DDOS/DOS attack in the following blog post:
WHAT IS A DDOS ATTACK IN BLOCKCHAIN? | THE TRUTH
I highly encourage you to take a look at it if you want more details about this kind of attack.
One of the most popular Blockchain attacks is the 51% attack. The 51% attack happens when an attacker has control over 51% of the block mining power. The block mining power change from one Blockchain technology to another depending on the type of used consensus.
For example, for the Bitcoin Blockchain, blocks mining power could be seen as the hashing power of the network. If a single or a group of nodes reach or surpass 51% of the whole network hashing power, then they would be able to continuously validate new blocks and manipulate the chain.
This attack requires a big investment in terms of either funds or technology. However, this proved to be feasible, with a 51% attack on the BTG blockchain resulting in significant losses in 2018. Unlike its fork Bitcoin protocol, BTG employs a variation of the Equihash algorithm instead of the SHA256 consensus method. However, an unidentified miner was able to seize more than 51% of the total BTG hashrate, which sparked the attack.
Another type of Blockchain attack that targets the consensus used in the Blockchain is the 34% attack. This attack is similar to the 51% in the fact that it tries to take full control over block mining by having a mining power of 34% over the Blockchain. However, the main difference between the 51% and the 34% attack is that the 34% attack target only Blockchains that use the Tangle consensus algorithm like IOTA Blockchain.
The team behind the development of the IOTA Blockchain is aware of this attack and they are working to solve this. However, with such a consensus problem, scalability might become difficult now for Blockchains that use this consensus. Being able to have a mining power of 34% nowadays, especially for newer Blockchain is relatively easy compared to the 51% attack. Therefore, the adoption of the Tangle consensus even with all its advantages might be slowed down until this problem is efficiently solved.
The Finney attack happens when a Blockchain user accepts a transaction that is not yet confirmed (added to a block). The idea here is that an attacker with two accounts A and B performs a transaction from A to B with all the amount of money that exists in A. then he adds this transaction to a valid block that he mine and doesn’t send it to the Blockchain network.
Then the attacker performs a purchase from a Blockchain user with account A and receives his goods before the transaction is added to a Blockchain. Then the attacker sends the first mined block to the network. At this moment, the first transaction that sends all the money from A to B gets validated before the purchase transaction gets to.
Mr. Hal Finney, the first Blockchain user to receive a Bitcoin first discussed this attack. It was the main reason for calling this attack Finney’s attack to honor him.
Similar to the Finney attack, this attack is based on the acceptance of the unconfirmed transaction. In this attack, the attacker sends two transactions at the same time. One transaction from account A to a merchant to purchase something and another one with higher fees to transfer all the funds from account A to B where B is another account controlled by the attacker.
As the fund’s transfer transaction is higher than the purchase transaction, then the fund’s transfer will be executed first. Which will leads to a double spending problem.
Double spending attacks like Finney and Race are based on the fact that users accept transactions before they get validated or confirmed. Therefore, to avoid those attacks, people should always wait for at least 6 blocks to be added to the chain on top of their transaction block before considering that transaction to be valid.
The idea of the Sybil attack is to create multiple identities to influence the network. The name of this attack was inspired by a 1973 book called Sybil, a woman diagnosed with dissociative identity disorder. With the proof of work consensus, this attack has no sense. However, when dealing with Blockchains that have some kind of voting system or anything else that can be influenced by the number of nodes in the Blockchain and their identity. Then this attack could be performed by creating multiple identities.
Many choices that have an impact on how the network operates are voted on in Bitcoin. By submitting a vote, miners and anyone who operates network nodes can decide whether or not they support a proposal. Attackers can vote for as many identities as they control if they create several identities on the network.
The Eclipse attack is another network-based Blockchain attack that targets the peer-to-peer infrastructure by trying to isolate a node or a set of nodes from communicating with others. The Eclipse attack can only happen in Blockchains with bandwidth restrictions that impede communication between all nodes.
A vulnerability to eclipse attacks is created by blockchain clients running on less powerful hardware preventing nodes from communicating. Once compromised, the hacker only needs to work with a small set of nodes that the infected node communicates with. By performing this attack the malicious nodes will be able to manipulate the kind of information that the targeted ones receive from the network.
For example, the malicious nodes could insert forged blocks that do not exist in the real Blockchain ledger and send the updates as if it is a real one to the targeted nodes. In this situation, even if the targeted node tries to verify if that information is real, the other malicious nodes will confirm it.
A DDOS attack or a distributed denial of service is a possible attack on the Blockchain too. Even if the main idea behind Blockchain technology is to avoid this kind of attack with the distributed nature of the network supporting the Blockchain, a DDOS attack is still possible.
I have already covered this kind of attack in a previous post with so many details on how a DDOS could be performed in the Blockchain, I highly encourage you to take a look at it if you need more information:
WHAT IS A DDOS ATTACK IN BLOCKCHAIN? | THE TRUTH
Most of the previously discussed attacks can lead to a Deny of service. A 51% attack for example could be used to drop all the incoming transactions. The mempool transaction’s fulfillment with fake transaction also leads to dropping all newer transactions leading to a DOS.
Finding a DOS vulnerability in the Blockchain client program used by nodes to communicate with each other or with users could also lead to a DOS attack if multiple exploitations of this vulnerability are performed at the same time.
Therefore, you should keep in mind that even the Blockchain network is susceptible to a DOS or a DDOS attack
The idea behind this attack is to exploit the network routing attacks to try to split the Blockchain network into two distinct Blockchains. This attack will result in producing two different chains with different transactions. At the end of the attack, all the transactions performed in the smallest chain will be eliminated.
Therefore, even if the transaction was previously validated and confirmed with 6 blocks. The transaction will still be rejected in the end. However, this attack gets difficult to be performed as the network gets bigger.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

Mobile app security Z. Oualid
Performing a penetration test against a mobile application before releasing it to the public is becoming more and more necessary to protect the user’s personal life. Compared to classic web ...


Copyright © 2020 Getsecureworld.

Post comments (0)