
What is a reentrancy attack in Solidity? | Technical examples
In June 17, 2016 the most famous DAO platform developed by solidity language was victim to a big hack that make it lose more than 3.6 million Ether. The attacker ...
blog + secure coding + Smart contract + Solidity Z. Oualid today

The transaction life cycle in most Blockchain technologies is mainly controlled by miners, even the order of the transactions. Therefore, when two users execute two different transactions at the same or closer time then only their gas fees will judge who will be executed first. This concept creates a vulnerability in smart contracts. So what is a transaction order dependence attack in smart contract?
The transaction order dependence attack in smart contract also called the Front Running attack, happens when a smart contract requires that, two transactions should be submitted and executed in the same order to get the same results.
In this blog post you are going to learn why this vulnerability exists in detail and how can an attacker exploit it. In addition, you will see in detail how you can prevent this vulnerability and fix it in your source code. All the discussions in this blog post will be accompanied by source code examples to better understand the concepts. So, if you are interested to learn more about this subject then just keep reading and leave a comment below.
The transaction order dependence attack in smart contract happens when a smart contract requires that two transactions should be submitted and executed in the same order to get the same results. This simply means that if two transactions are submitted to the smart contract, then the final state of the smart contract will depend on which one of them was executed first.
Let me give you a technical example to better understand this concept. Let’s say there is a smart contract that allows people to offer their precious objects for sale. In this smart contract, the owner can change the price of his object at any moment he wants to. In addition, the smart contract allows other users to buy those objects by sending the specified sell price.
You may not notice the vulnerability in this scenario, the owner of the object may send a price changer transaction, to the smart contract at the same moment the buyer does to get the object. However, the gas price for the owner transaction is more than the buyer transaction gas price.
In this situation, the owner might be able to make the user pay more than what he was expected to do because his transaction will be executed first.
If you can’t see the impact of this vulnerability with this example, please take a look at the following section where you will get 2 smart contract codes that are vulnerable to this attack.
To better understand the concept of this vulnerability, I suggest you take a look at the following smart contracts source codes:
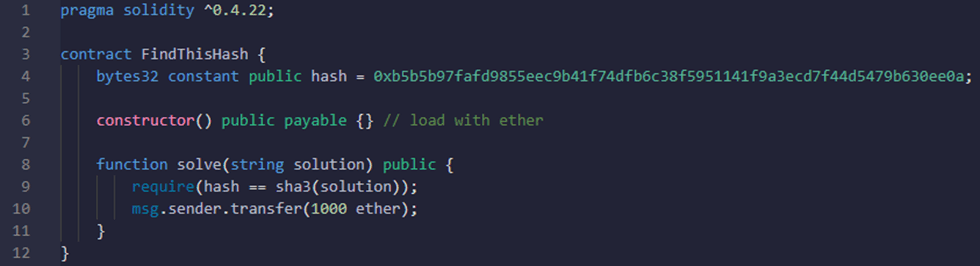
In this example, the smart contract offers the user the ability to win 1000 ether if he was able to find a string with the hash specified as the variable “hash”.
This smart contract is vulnerable to a transaction dependence vulnerability and the attack could be like the following:
Like most smart contract vulnerabilities, the impact of the transaction order dependence vulnerability depends on the business logic of the smart contract. In most real-life cases, the impact is low or medium, unless there is some sort of financial loss to either the smart contract or the users.
Many tools were developed by security researchers who are capable of discovering this kind of vulnerability. Therefore, here is a list of some of the most used ones to discover this vulnerability:
For more details on what other types of vulnerabilities can each tool discover, you can check my previous blog post.
If you don’t like to use the tools and you want to try to find those vulnerabilities manually, then here are some things you should look for while auditing your smart contract:
Preventing this type of vulnerability is quite difficult compared to others, as it may require big business logic changes sometimes. However, the commit/reveal schema can be used to solve the issue. To better understand this concept let’s try to fix the previous vulnerable code discussed in the second section of this blog post.
Here is the vulnerable code:
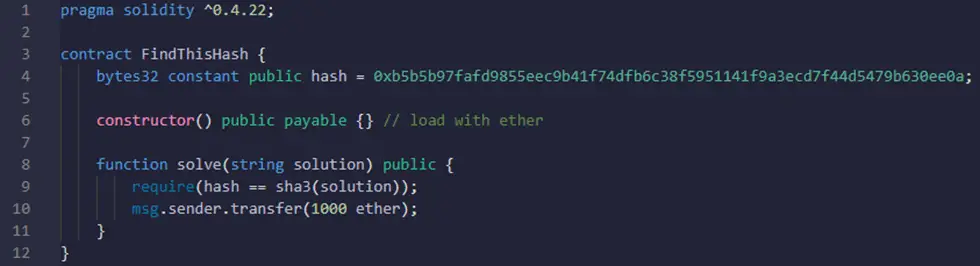
As we said in the previous section, the solve() function of this smart contract is vulnerable to the transaction order dependence attack. Therefore, here is a fixed version of this smart contract:
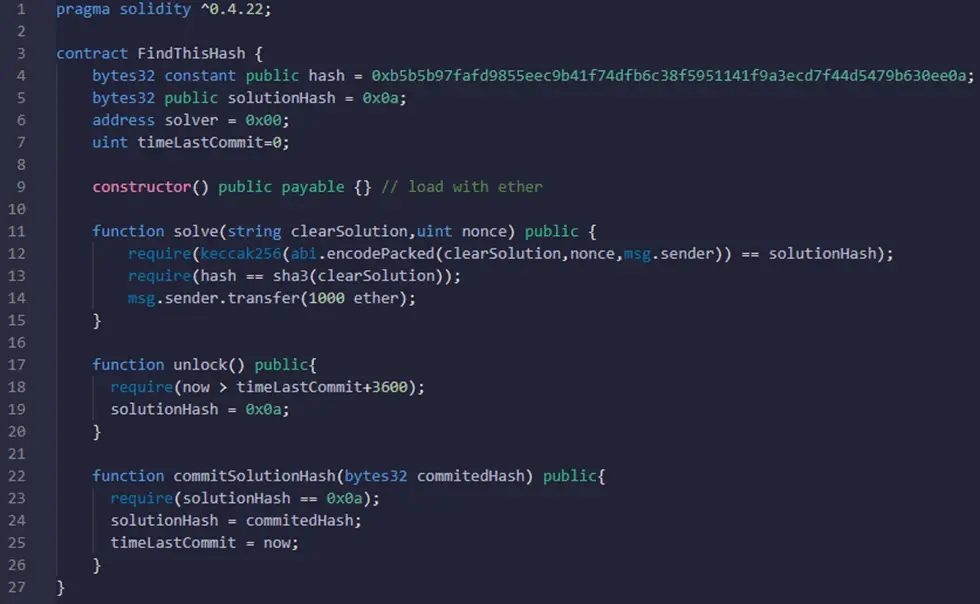
Let’s analyze these smart contract functions:
Using a hash instead of the actual solution protects the user from leaking his solution in the Blockchain ledger.
All the Blockchains that give the nodes the ability to reorder the transactions could have this vulnerability in their smart contract codes. However, Blockchain like Solana which uses the proof of history to create the order, may not be vulnerable to such attacks.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

blog Z. Oualid
In June 17, 2016 the most famous DAO platform developed by solidity language was victim to a big hack that make it lose more than 3.6 million Ether. The attacker ...



today
blog + secure coding + security solutions + Smart contract Z. Oualid
Undoubtedly, ChatGPT stands out as one of the most remarkable inventions of 2021. Its wide-ranging capabilities and applications have opened up endless possibilities for human interaction and problem-solving. Furthermore, certain [...]
Copyright © 2020 Getsecureworld.
Post comments (0)