Acunetix is one of the most popular web application vulnerability scanners in the market. It is known for its quick scans and a number of features that make it suitable for standards and laws compliance. However, a lot of people ask if Acunetix is safe?
Acunetix is not a safe tool when it is used against a web application running in a production environment with an authenticated scan.
In the following blog post I am going to explain in detail what makes Acunetix not safe, and how you can use it in a safer manner, and when. So if you are interested just keep reading.
I will have to explain first how web application vulnerability scanners work including Acunetix so that you can understand why this tool is unsafe. If you already know about the work of vulnerability scanners then jump directly to the “What makes Acunetix an unsafe tool” Section.
How Acunetix works?
Most dynamic web application vulnerability scanners in the market work using one of the following techniques:
Fuzzing the application using a knowledge database
In this technique, the tool tries to send multiple values to the application based on the database it has and that was fed a number of well-designed inputs. All those inputs were designed to try to trick the application to perform a strange behavior. As a strange application behavior is most of the time a sign of a possible vulnerability in the application.
A strange behavior could be as simple as crashing the application or showing some sensitive data due to a debugging mode enabled in the app.
Using this technique the vulnerability scanner gets quicker and finds a good number of basic vulnerabilities. However, this test speed comes at the cost of low code coverage, which reduces the effectiveness of the scanner.
Tracking the user inputs to see if it gets to a dangerous function in the application
This is the most effective technique to discover pattern-based vulnerabilities and it is called data flow analysis. The idea is to send specific data to user input and track this data in the application to see if it reach a dangerous function in the app.
This technique has a great code coverage compared to bland fuzzing which means detecting multiple types of pattern-based vulnerabilities. However, this code coverage comes at the cost of a very slow scan that in some cases can become useless due to the complexity of the application.
No matter what technique the scanner will use, a spidering phase is required to start the tests. In spidering phase, the scanner tries to collect information about the application parameters and pages. To do that, the scanner starts to browse any link it finds on each newly discovered page and then saves their parameters to be tested later.
What is an authenticated scan?
When performing a vulnerability scan, you can do that both in a black box mode or a gray box. In the black box scan, the scanner tries to do the same work as a simple visit to the application. However, in the gray box the scanner act like an insider who has the actual credential to access private spaces.
Of course, performing an authenticated login will open more paths for the scanner to discover and test, which is a good thing, and it actually enhances the code coverage for the scanner.
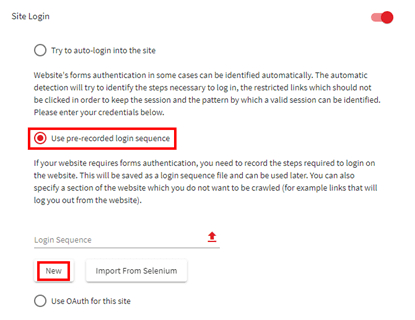
Acunetix is very good at this level, as it offers many features to perform a correct login to the app. Even if you have a captcha in the login form, Acunetix offers a manual authentication system to solve this issue for you.
Moreover, if the application has some sort of login sequence, Acunetix offers a way to do that to correct log in to the app.
What makes Acunetix an unsafe tool?
Usually, login interfaces are placed to protect some important spaces of the application. They can be admin interfaces or even a simple user interface. That means more links for the vulnerability scanner to discover. In other words, more links to the spider.
Most of the time, those interfaces have some critical links that could perform some modifications to the data stored in the application. For example, we can find a button or a link that removes a user or perform a transaction.
Here is why Acunetix is an unsafe tool. If you launch this tool with an authenticated scan, during the spidering phase, any link in the application will be executed. This means that even the links for removing users or editing data will also be executed, which can make a serious impact on the application data.
in addition, the data injected by Acunetix is designed to crash the application, which mean it can in some cases make some modifications to the actual data stored in the database (SQL injection case).
How can you make a safe scan with Acunetix?
It is very difficult to control a spider in a production environment if the scan is authenticated. It is always recommended to perform an authenticated scan in a test environment. However, if the test should be performed in the production environment, then the only thing you can do is to disable the dangerous pages from being scraped by the spider.
It is true that this technique will make Acunetix safer, but this is at the cost of less effective in terms of discovering vulnerabilities. The best and the most recommended action is to run the Acunetix tool in a test environment, this way you will be 100% sure that no data get altered during the scan.
In addition, before you launch any kind of automated scanners you should always take a full backup of both the application and the database. In some cases to test the existence of some vulnerabilities for example the File upload ones, the scanner tend to created some PoC files in the web application.






Post comments (0)