
What is the best consensus algorithm?
When building a Blockchain solution for a company or an organization, one of the decisions that the architecture may need to take, is choosing a consensus algorithm. So what is ...
Some of the most popular consensus algorithms are Proof of Work and Proof of stack. Those algorithms have proven their efficiency and security over time after years of being implemented in the most known Blockchain. Therefore, what is the difference between PoW and PoS?
Proof of stake is a consensus technique that is used as an alternative to Bitcoin’s proof of work. The absence of costly computations and hence a reduced entry barrier for block generation rewards are the key claimed advantages of proof of stake systems. However, the Proof of stack concept suffers from many possible attacks that do not exist in the PoW and requires more security mechanisms to solve these issues.
In this blog post, you are going to see the main differences between those concepts and the pros and cons of each one of them. Moreover, we are going to see the most popular variations of those concepts that try to enhance them, and where they are used.
Knowing more about how those concepts work and where they are implemented, will help you better understand the Blockchain‘s work to quickly identify their security weaknesses. Therefore, if you are interested, just keep reading.
Here is a table that summaries the key differences between the Proof of work and the Proof of Stack:
| Proof of work | Proof of Stack |
| High energy consumption | energy-efficient |
| Built on the idea of machines has a computation limit no matter how powerful it is | Built on the idea of if someone has a stake in the system, then they will not try to sabotage the system |
| Wining the right to add a block to the Blockchain depends on your computation power | Wining the right to add a block to the Blockchain depends on your stacked value the more you have the better it is |
| Competition based selection to validate transactions | Pseudo randomly selection to validate transactions |
| Takes More time to validate new blocks than PoS | Takes less time to validate new blocks |
| Tested for a long time and proved efficiency | Not well tested |
In the following part of this blog post, we are going to dig deeper into the technical differences of these two consensus concepts. In addition, you will get an idea about the most popular variation of those concepts and their popular implementations.
The proof of work is an old mechanism that has been first implemented as a way to protect against DDOS attacks for web services by Adam Back in May 1997. The general idea is pretty simple, the user is given a digital puzzle that needs to solve so that he gets access to that resource each time he wants to.
In the Blockchain, this concept was implemented in Bitcoin as a way to implement a distributed timestamp server on a peer-to-peer basis. In this whole blog post, we are going to discuss how this concept was implemented in the Bitcoin Blockchain as this is the most actual popular use of this system. However, this concept might be very different in other applications like DDOS protection and others.
The proof of work concept in the Bitcoin network can be translated to the following equation:
H (nonce || previous hash || Tx || Tx|| . . . ||Tx) < Threshold value
This means that to validate a new block, the node should find a nonce (a piece of data) that when combined and hashed with the header of the previous block and all the new transactions give a value lower than the threshold value.
The threshold is simply a hash string that starts with a pre-defined number of zeros. The number of zeros that threshold will have in the Blockchain depends on the Blockchain calculation power. This means that each time Blockchain starts to validate new blocks faster (number of validated blocks per week for example get high) the number of zeros is incremented to make it difficult to find the nonce.
Here is a diagram that summaries this algorithm:
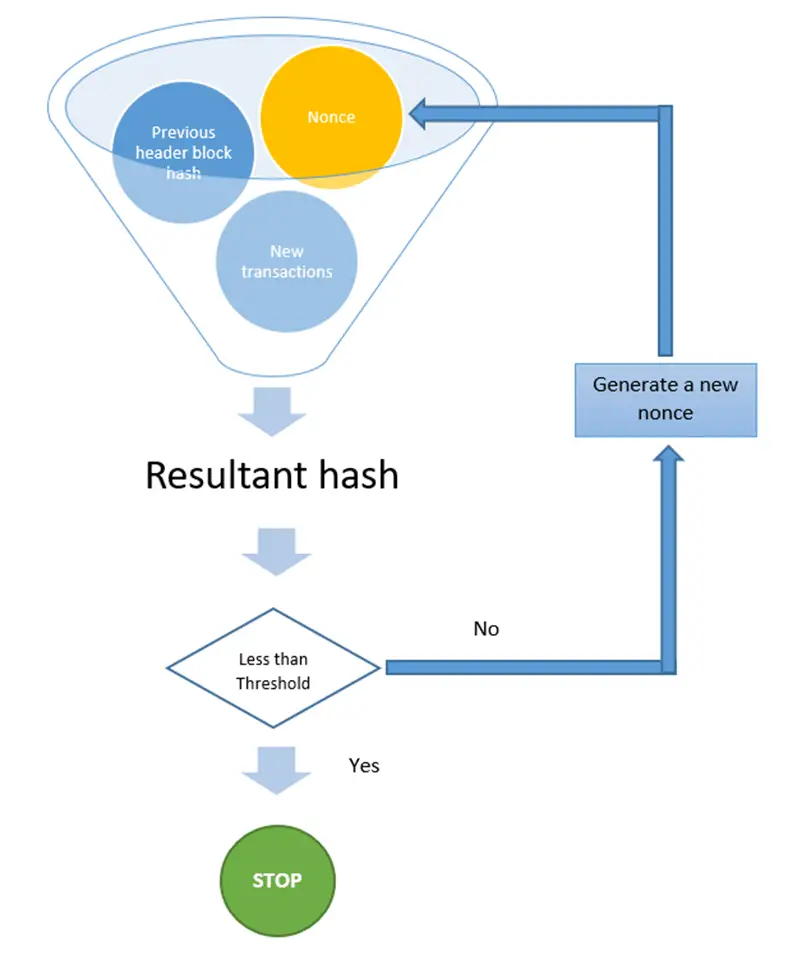
In the context of Bitcoin, once the Nonce is discovered, the new block is broadcasted to the whole network. The other nodes show their acceptance of the block by mining on the next block in the chain, using this block header hash.
As mentioned in previous blog posts, Proof of work has a big drawback related to energy consumption. The more nodes join the network, the more it becomes harder to find the puzzle solution and validate the transactions.
Therefore, to solve this issue a new consensus algorithm based on the proof of stack concept was proposed. This concept is based on a pseudo-random election to choose the node that will validate the next block.
The idea behind this concept is pretty simple, if a node has invested (stacked) so much money on the Blockchain, then he will be less likely tends to destroy it as this will cost him more than what he may gain from his attack.
Therefore, the more a node has stacked money on the Blockchain, the more he will have the chance to validate new blocks.
In some popular Blockchain networks like Cardano, the Follow-the-Satoshi (FTS) algorithm is used to find the node that will validate the next block. The FTS algorithm is a hash function that takes a random string as an input (it might be as simple as the previous block header) and then the function generates the index of a certain token in the Blockchain. Then the owner of this token is the one that will be chosen to validate the next block.
The probability pi that node i is selected to be the leader in a network of N participants is:
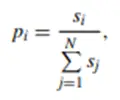
Where si is the stack of node i. If you need more details about this concept, I highly encourage you to take a look at the work done by CONG et al. in their paper.
This equation explains the words we said in the beginning, the more tokens you own in the network, the more chances you get to validate the next block.
Personal idea:
The fact that the leader or the node that will validate the next block is chosen in a pseudo-random way adds more security to the network compared to the PoW. Think about it.
Let’s suppose that a 51% attack was successfully conducted in the PoS Blockchain and there was some fraud in the Blockchain. Having a random algorithm means that even the smallest node (in terms of the stack) of the Blockchain has a certain probability to become a leader at some point.
Therefore, once this node gets the lead and checks the transaction it will discover and report the fraud. This means the attacker will be penalized and lose more than what he made from his attack sooner or later. This is why each node in the PoS based Blockchain has more interest in working correctly than performing an attack.
However, this is not possible in the PoW consensus, as if the 51% attack happen, and the calculation power was supported to get more and more powerful than the whole network, the leader will always be the same.
Of course, this is just theory and it is very difficult to be performed in reality but it is still a risk.
The proof of work consensus concept was the first technique used in the Blockchain to protect Bitcoin. Therefore, this concept has proven with the time test that it is very secure and efficient.
However, when talking about other aspects that a Blockchain needs to offer to its users rather than security, you can clearly see that this consensus is not really very efficient. The computation process requires a high computation power, which means more energy to consume. Therefore, more negative impact on the planet.
Moreover, this concept takes more time to validate new transactions which may make it useless for quick real-life payments. In addition, the more nodes get into the Blockchain to validate new blocks, the more it gets difficult to solve the digital puzzle. Therefore, at some point in the Blockchain life, the miner’s nodes in the Blockchain will reach a plateau where mining will no longer be lucrative.
The proof of stack concept was created to actually solve the PoW limitation, especially in the time required to validate new blocks and the energy consumption. As mentioned in the previous section of this blog post the PoS algorithms do not rely on computation power, which means anyone can be part of the network even with less expensive computers. Therefore, more decentralization for the Blockchain as more nodes will join the network. This also means less energy consumption.
The tests of this concept have shown that validating new blocks takes just around 1min, which is way lower than the proof of work that requires 10 min for new blocks to be added.
Unfortunately, this concept is still new and it was not very well tested compared to the proof of work, in terms of would he stay efficient even after 10 years from now or not.
Because of the randomness aspect in the new validator choice, and as I said earlier, in my opinion, this concept is more secure than the proof of work when dealing with the 51% attacks.
CPU-bound PoW is a kind of PoW in which the amount of processing required to solve the cryptographic hash problem is proportional to the calculating speed of the CPU or other hardware, such as ASICs. It is simply the proof of work that we all know about and which is implemented in Bitcoin and many other Blockchains.
PoW could also be provided by memory-bound PoW algorithms, which rely on system RAM. The performance of the memory is controlled by its access speed or its capacity. These PoW algorithms are ASIC-resistant due to their dependency on memory. Equihash is a memory-bound PoW algorithm that is widely used.
The chain-based Proof of stack mechanism is a very similar type to the PoW. Here the nodes need to solve a digital puzzle, but without consuming the computation power. Rather than competing to solve the hashing challenge by using a large amount of power and specialized technology, PoS solves the hashing puzzle at regular intervals based on the clock tick. If the minter’s stake value is high, a hashing challenge gets easier to solve.
Using a verified random function (VRF), a group of stakeholders is randomly chosen in this system. This VRF generates a random set of stakeholders depending on their stake and the current state of the blockchain once it is activated. The chosen stakeholder group is now in charge of proposing blocks in the correct sequence.
DPoS is extremely similar to committee-based PoS. However, there is one major distinction. The group of stakeholders is chosen through stake delegation rather than using a random method. The chosen group consists of a certain number of minters who work in a round-robin method to manufacture blocks. Users of the network vote to choose the delegates. Participants’ share in the network is proportional to the number of votes they have.
Here is a table that can give you an idea about what consensus is used in which Blockchain:
| Proof of work | Proof of stack |
| Bitcoin | Ethereum |
| Litecoin | Cardano |
| Dogecoin | Tezos |
| BNB | |
| Solana |
The BNB cryptocurrency uses a consensus mechanism called Proof of Staked Authority consensus architecture (PoSA). This consensus combines both the proof of authority (PoA) and the proof of Delegated PoS (DPoS)
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

Blockchain Security Z. Oualid
When building a Blockchain solution for a company or an organization, one of the decisions that the architecture may need to take, is choosing a consensus algorithm. So what is ...



today
blog + secure coding + security solutions + Smart contract Z. Oualid
Undoubtedly, ChatGPT stands out as one of the most remarkable inventions of 2021. Its wide-ranging capabilities and applications have opened up endless possibilities for human interaction and problem-solving. Furthermore, certain [...]
Copyright © 2020 Getsecureworld.
Post comments (0)