
What is the most common Web security vulnerability?
One of the most common questions that I get from my students when I do my penetration test course is what is the most common web security vulnerability? After years ...
Web servers are becoming more and more the first target for attacks. This focus comes from the fact that web servers are the most exposed servers in any company network. In addition, taking control over the webserver could be the first access point to the local network of the victim.
Here is the most common web server attacks:
Asking this question means, that you are in one of the following situation:
Don’t worry I’ve been there once, and yes in the three situations, each time with a different client. Therefore, if you are interested in knowing more about those attacks then just keep reading.
Here is my general vulnerabilities stack:
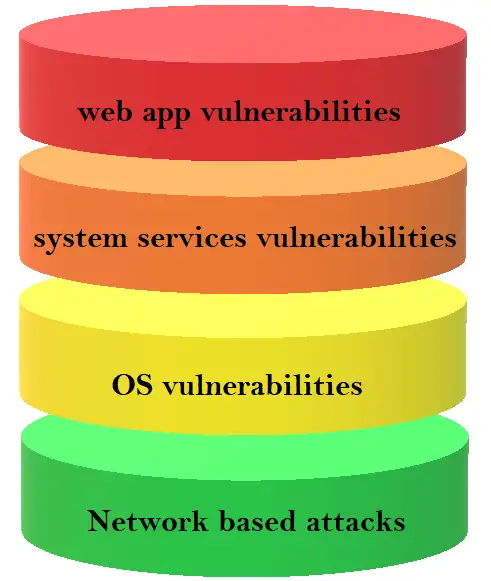
The number one attack surface for a web server is their hosted apps. In general, the web applications hosted by the server are less secure than the web server itself. In other words, web applications contain more vulnerabilities than the webserver.
Not all the vulnerabilities that affect a web application have an impact on the hosting server. However, many of them have. In the following paragraphs, I will give you some examples of vulnerabilities that have a direct impact on the server.
Command injection vulnerability happens when the application fails to filter the user inputs injected in a legitimate command executed by the application. Using the user’s input without filtering it in a legitimate command gives the attacker the possibility to execute any system command.
If you have never seen this before, and I fully understand that as this kind of vulnerability is getting rarer, then you may think that this is an unrealistic vulnerability. However, here is a real example that was once very popular for this kind of vulnerabilities.
In the routers, firewalls, and in general any network equipment, it is very common to find a web interface that you use to test connectivity. In general, it performs a ping or a traceroute to an address you specify. Therefore, not filtering or weak filtering of the IP address the user give was giving the attacker the ability to inject and execute system commands.
The SQL injection vulnerability happens when user input is directly injected into a legitimate SQL request. Actually, this is one of the underestimated vulnerabilities. I usually ask my students this question:
How deep a hacker could go in exploiting the SQL injection?
And it is rare when someone thinks that he might be able to execute System commands. Yes, you heard me, this vulnerability could be exploited in some conditions to take full control over the whole hosting server.
For example, let’s suppose that you have a web application that uses SQLserver as a Database management system. Now, if your application was vulnerable to SQL injection then, the attacker could use the xp_cmdshell SQL function that gives him the ability to run system commands.
It is more likely that the SQL server gets launched using admin privileges. Therefore, the attacker will be able to run the commands using the admin permissions, which means full control over the server.
The second web server attack comes from the server service handlers, for example, HTTP or FTP or any other service running. One of the first steps that a hacker starts with when trying to infiltrate a company is performing reconnaissance and a port scan. The idea behind performing the scan is to find the open ports that run vulnerable services.
Most of the time, companies forget to perform updates to their servers or they just cannot apply them because of application dependencies. Therefore, finding a vulnerable service to exploit is also very common.
Just to give you an idea about this aspect, I would like to give you some examples of some very popular vulnerabilities that were widely exploited by hackers years ago.
The FTP server VSFTPD v2.3.4 has a Backdoor Command Execution vulnerability that was very common in 2011. Successful exploitation of this vulnerability gives the attacker full control of the hosting server.
You need to know that, vulnerabilities could also be the result of a wrong configuration of clean services. I mean it is very common to find for example default passwords used in an FTP server or a misconfigured SMTP server that allow commands like the EXPN and VRFY commands. if these commands have not been disabled by the system administrator, they can be used to enumerate system users.
A vulnerable operation system can also be a victim of attacks. However, in most cases, the Operation system vulnerabilities can only be exploited locally for example to do privilege escalation to get root privileges for example.
Also, the operation system vulnerabilities could be related to wrong configurations or forgotten critical files.
Durtycow is one of the most popular and critical OS Linux-based vulnerabilities that was discovered in 2016. A successful vulnerability could give simple system users like www-data (default user of a hosted web application) root control over the host.
Moreover, creating a file with root privileges that has read, write, and execute privileges and a setUID flag, is a critical vulnerability that can be used to do privileges escalations in the system.
In some cases, the objective of the attackers is not to take control of the hosting server. Sometimes, because taking control may take too much time and resources. Therefore, attackers use some network attacks to disturb the normal operation. This usually leads to some critical business losses due to downtime.
One of the most common attacks performed usually by botnets is the Distributed Deny Of Service (DDOS) attack. One of the most popular DDOS attacks was performed in 2016 by the Mirai botnet.
Sometimes black hat hackers could try to hack routers that connect the victim’s webserver to the internet to perform traffic redirection and collect user’s information.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

blog Z. Oualid
One of the most common questions that I get from my students when I do my penetration test course is what is the most common web security vulnerability? After years ...


Copyright © 2020 Getsecureworld.

Post comments (0)