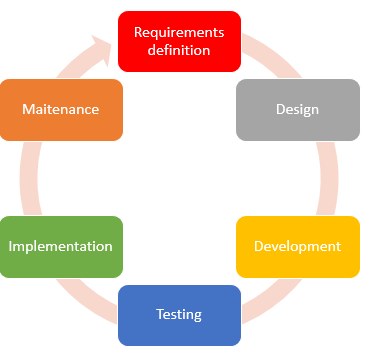
How many steps are there in a secure development lifecycle?
For many years ago, cyber security was considered as a final product or job that you add when the application functionalities are correctly working. However, today the game has changed ...

For many years ago, cyber security was considered as a final product or job that you add when the application functionalities are correctly working. However, today the game has changed ...

One of the most frequent questions that I get from my client, especially those who use Godaddy as a hosting service is this, what do you think about Godaddy’s website ...

For many years, one of the most confusing vulnerabilities for both security professionals and clients in the industry is the Directory path traversal and the file inclusion (LFI/RFI). So what ...

After years of doing penetration tests and working with many companies, I have started to notice that this question start to become more frequently asked especially from those with complex ...

DevSecOps is one of the most in-demand fields in the industry of cybersecurity. Most companies that I worked with are thinking or start to implement this process in their daily ...

CVE is a very popular word in the cyber security industry. If you take any penetration test or any vulnerability assessment report, you will find a bunch of CVEs for ...

Every time I give my penetration test report to my client to start fixing their vulnerabilities, the first question they ask, is which one we should prioritize in our fixing ...

One of the most critical incident that could happen to a website owner, is to find his website blacklisted. According to some researches, this blacklisting leads to more than 90% ...

If you have already performed a penetration test on your website or your network infrastructure, then you should have heard about the scope of the penetration test. Defining the scope ...

XSS vulnerabilities are one of the most popular security issues on the web. Unfortunately, even if the new development technologies have done their best to eliminate this vulnerability, it still ...