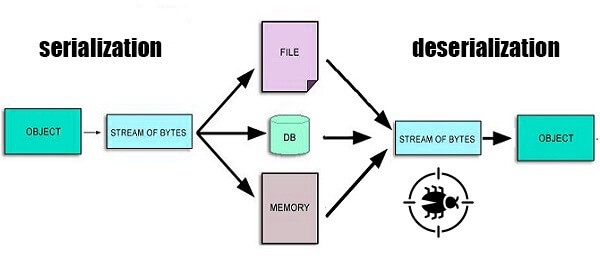
What are the most common mobile apps vulnerabilities?
In the intricate world of mobile app development, where functionality meets vulnerability, understanding the common weak points is key to fortifying your digital creations. As developers and app owners, navigating the landscape of potential threats is a vital aspect of ensuring robust cybersecurity. So, what exactly are the mobile apps’ ...