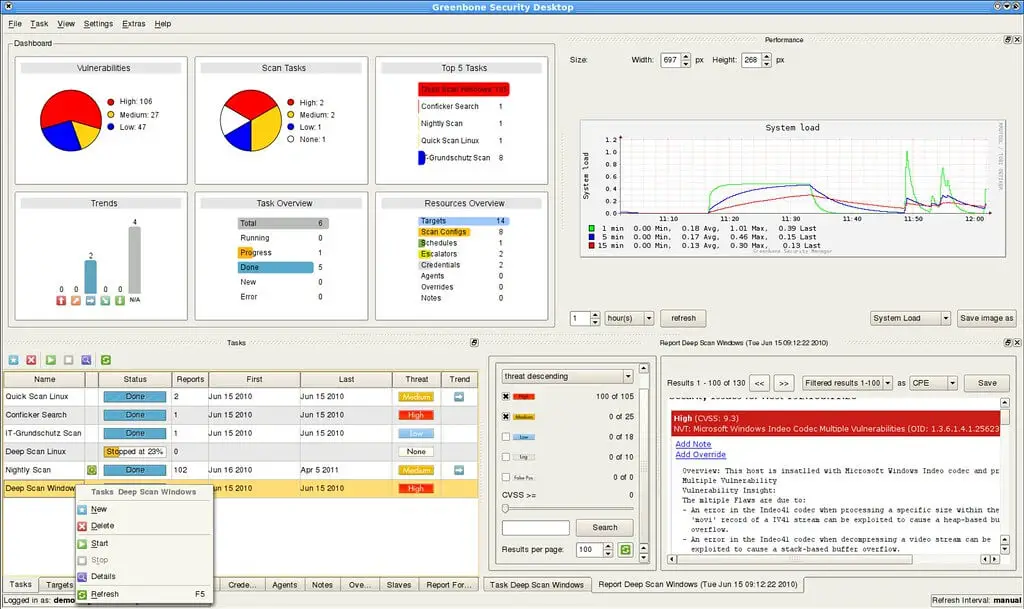
The difference between Cyberrange and CTF
Embarking on the cybersecurity journey often feels like navigating a complex maze, where different training environments beckon enthusiasts with promises of skill enhancement. While Capture The Flag (CTF) competitions have long been hailed as a dynamic battlefield for honing practical skills, the emergence of CyberRanges adds a new layer to ...