
How to practice penetration testing safely?
Practicing penetration testing legally was always a difficult thing to do while learning this skill. This problem did exist years ago where even the information was not so organized and ...
DDOS attacks are one of the easier and most popular attacks that can a website or server in general faces. The number and the power of those attacks are at rising years after years due to the number of vulnerable devices that get connected to the internet. Therefore, everyone needs to be aware of how to stop this attack and protect their website.
How to stop a DDOS attack? The DDOS attack could happen at 3 levels of the network structure (application, network, and protocol). Therefore, here is a list of checks and techniques to stop a DDOS attack exploiting each of these levels weaknesses:
In the following sections of this blog post, I am going to explain in detail how you can perform each of these actions. This blog post will only focus on the situation where mutual and VPS hosting are used as these are the most common ones on the internet. In addition, these situations are the most difficult ones as very few options are possible due to lake of control over the server and the network around it. Therefore, if you are in one of those situations then just keep reading.
Before we start talking about what we can do to stop a DDOS attack, I would like to first explain what are the types of DDOS attacks. Understanding those types will make a big difference in choosing the right technique to stop a DDOS attack that is happening.
The DDOS attacks are divided into three main types:
Application-based DDOS happens when an attacker exploits a known or unknown vulnerability in one of the server applications and services to crash the system. In most cases, those vulnerabilities have a relation with memory management, which leads to a system data overwrite and crash.
The network or volume-based DDOS attacks are the most common ones and try to flood the victim server with a high volume of requests per second. In general, this type of attack requires a large number of devices called botnets to have a real impact on big companies. However, this type also can successfully make a medium or small website out of service.
Protocol-based DDOS attacks happen when the attacker exploits a protocol logic to make a deny of service. Also, this kind of attack requires a large botnet to successfully make a big website out of service. However, the protocol-based attack does not require power as much as the volume based one. In addition, it is more effective than volume-based and might be able to even bypass firewalls.
As I said in the first section of this blog post, a DDOS attack could be exploiting a known or an unknown vulnerability in one of the server applications. Unfortunately, this type of attack can easily bypass firewalls and cause the denial of service.
Therefore, discovering this attack is the most difficult as finding the exact request that causes the denial of service requires a deep analysis of the server and application logs.
Here is a list of files you should examine and analyze to find exactly what request has caused the crash:
The files that I have listed here are not the only ones that you can investigate, they are just the ones that you may have access to while using a mutual or VPS server. In addition, most of the files listed here are related to PHP applications and frameworks. Therefore, if you are using another development technology then you just need to look for the equivalent files.
As you can see the folders and files presented in this list touch different elements of the hosting server, as the application-based DOS attack can be the results of either the web application, the web server itself, or the host services.
In the web application logs, you should look for all the events that happened just before the crash and investigated each one of them. The objective of those investigations is to figure out what part of the source code, has caused the crash to identify the vulnerability.
Identifying the exact vulnerability will give you the ability to fix it and avoid the DDOS attack once for all. Therefore, performing regular penetration tests or creating a bug bounty program, significantly helps you avoid this problem, by anticipating their discovery by good hackers.
After discovering the vulnerability that causes the DOS attack, a new process starts. This process has the objective of rather eliminating the vulnerability by correctly fixing it in the app, or mitigating the risk if the fixing is not feasible.
For some of you, this might be strange but it is not always possible to fix a vulnerability. A lot of big companies just leave those less critical vulnerabilities without patches. However, what they do is they make a mitigation technique or solution. I have already explained in detail how this can be done in the following blog post 10 things to do when you can’t fix a vulnerability
The first question that all my clients ask when they start to fix the vulnerabilities is do I need to shut down my website while fixing the vulnerability? Shutting down the website is the best option to eliminate any compromising risk. However, this option is not always possible as it might cause some serious financial losses. Therefore here is what you should do to keep using your website and fixing the vulnerabilities at the same time while reducing the compromising risks:
Unfortunately, most of the DOS vulnerabilities exploits evolve in time to become Remote code execution, which makes them very critical. Therefore, I highly recommend doing whatever it takes to correctly fix these kinds of vulnerabilities.
Using a CDN service is a great solution to mitigate DDOS attacks while accelerating the loading of your website. In addition to the distributed architecture of those CDN that by default perform a sort of load balancing to mitigate a DDOS attack, most CDN services put in place DDOS attack mitigations solutions.
I am not going to discuss what those solutions are, as this cannot be affordable or feasible when dealing with a mutual hosting service or even a VPS. However, I will explain some of the options offered by those CDNs to enable DDOS attack preventions techniques.
Under attack is a mode offered by Cloudflare to mitigate DDOS and other attacks. The main idea behind the Under attack mode is to put in place a Javascript web page between the visitors and the actual website. The javascript page blocks the visitor from accessing the website utile he solves a captcha.
This technique is very efficient and will block the DDOS, bruteforce, and other attacks from reaching the actual server where the app is hosted. However, this technique is only efficient when dealing with the Volume and some protocol-based DDOS attacks as they become efficient only if they are automated. Unfortunately, an application-based DDOS attack can easily bypass this technique as the attack can manually exploit the application vulnerability to crash it.
To enable the under attack mode, all you have to do is to:
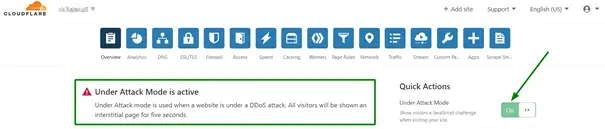
For more details, you can take a look at the Cloudflare support documentation.
One of the solutions you can do to stop a DDOS is to block the IPs source of the DDOS attack. The idea is to take a look at the IPs that send a lot of requests to your applications and try to block them for a certain amount of time. To identify those IPs you can use your own apache logs or the tools offered by your Cpanel.
Here are the tools and the files you can check to retrieve this information:
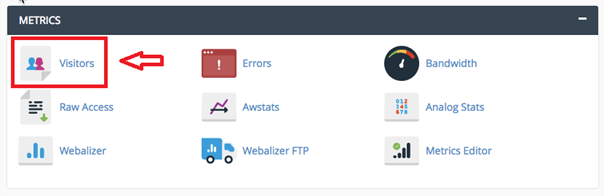
Until now all you have done is to identify the suspicious IP address. Next, you have to block those addresses, and to do that you can use either the Cpanel tool called IP blocker:
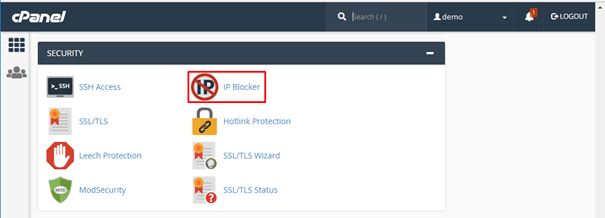
Or by configuring the apache server to block those IPs. The idea is to create a file called block-offending-ips.conf with the right configuration and put it into the /etc/conf.d folder.
Here is a detailed explanation of this solution explained by the adobe help page
To be honest, this technique is inefficient especially if it is performed without using an automated tool. Usually, when an attack performs a DDOS attack, the botnet used for this attack has a very large number of IP addresses and in many cases, those IP attacks change over time. Therefore, blocking those IP addresses manually, will not be always feasible and efficient.
Another enhanced solution for the IP blocking technique is to block a whole Geolocation. For example, if after analyzing the files you discover that those attacks come from country X then you can block all the requests that come from it.
First and after you have listed the IPs you discovered using the techniques explained in the previous section, you will need to get their locations. To do that you can use any web application that provides this service. There is many websites out there that offer this service for free, and here are some examples:
I highly recommend using multiple solutions to verify as the accuracy of those solutions is not very good.
Once you get the right Geolocations for those IP addresses, all you have to do is to block them using either:
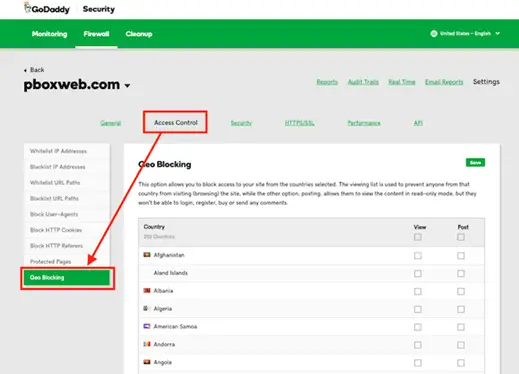
I have the same idea for this solution too, and I consider it not efficient. The reason behind this point of view is that the botnets used in a DDOS attack could have devices from the whole world. Therefore, blocking a country or two will not solve the issue.
If you are using a GoDaddy host, then by default you will have a DDOS mitigating solution offered by GoDaddy even if you didn’t buy GoDaddy’s security solution. This solution is called “Emergency DDOS Protection” the main idea of this feature is to cut the DDOS traffic in half by disabling the POST requests.
Now, if you have a blog or a static website where all that a visitor will do is navigating through the website to see different articles and posts, then this is a good solution to reduce the impact. However, if you have an e-commerce website, then this may cause serious financial losses as no actions would be performed on the website.
When using a CDN solution, then this makes it difficult for an attacker to cause a serious impact by using a volume or protocol-based DDOS attack. Therefore, attackers tend to perform what we call a CDN bypass, to leak the actual server IP address where the application is hosted.
By knowing this IP address the attacker can send his requests directly to that server and bypass all the CDN protections. Therefore, to protect your website from such attacks, you will need to block any direct access to your website by adding the following configuration to your .htaccess file:
<FilesMatch “.*”>
Order deny,allow
Deny from all Allow from 192.88.134.0/23
Allow from 185.93.228.0/22
Allow from 2a02:fe80::/29
Allow from 66.248.200.0/22
</FilesMatch>
The IP address mentioned in this configuration is related to Godaddy’s CDN solution. Therefore, if you are using Cloudflare or any other solution you will need to look for their IP ranges and replace them in this configuration.
Another technique used by attackers to find the right server IP address when the website uses a CDN is through the email service. If you are using an email server in the same server where the app is hosted, then receiving an email from your server, the attacker can retrieve the original IP address.
Therefore, it is recommended to install this server on a whole different server, to avoid this kind of attack.
Written by: Z. Oualid
I am a Cyber Security Expert, I have worked with many companies around the globe to secure their applications and their networks. I am certified OSCP and OSCE which are the most recognized and hard technical certifications in the industry of cybersecurity. I am also a Certifed Ethical hacker (CEH). I hope you enjoy my articles :).

blog Z. Oualid
Practicing penetration testing legally was always a difficult thing to do while learning this skill. This problem did exist years ago where even the information was not so organized and ...



today
blog + secure coding + security solutions + Smart contract Z. Oualid
Undoubtedly, ChatGPT stands out as one of the most remarkable inventions of 2021. Its wide-ranging capabilities and applications have opened up endless possibilities for human interaction and problem-solving. Furthermore, certain [...]
Copyright © 2020 Getsecureworld.
Post comments (0)